How To Create Business Value Through Trust.
Trust is one of the most pressing concerns for all B2B software companies today. In this white paper, we'll explain why that's the case and suggest how you can earn the trust of your customers using a business-focused definition of trust and a framework that addresses your customers' key concerns.
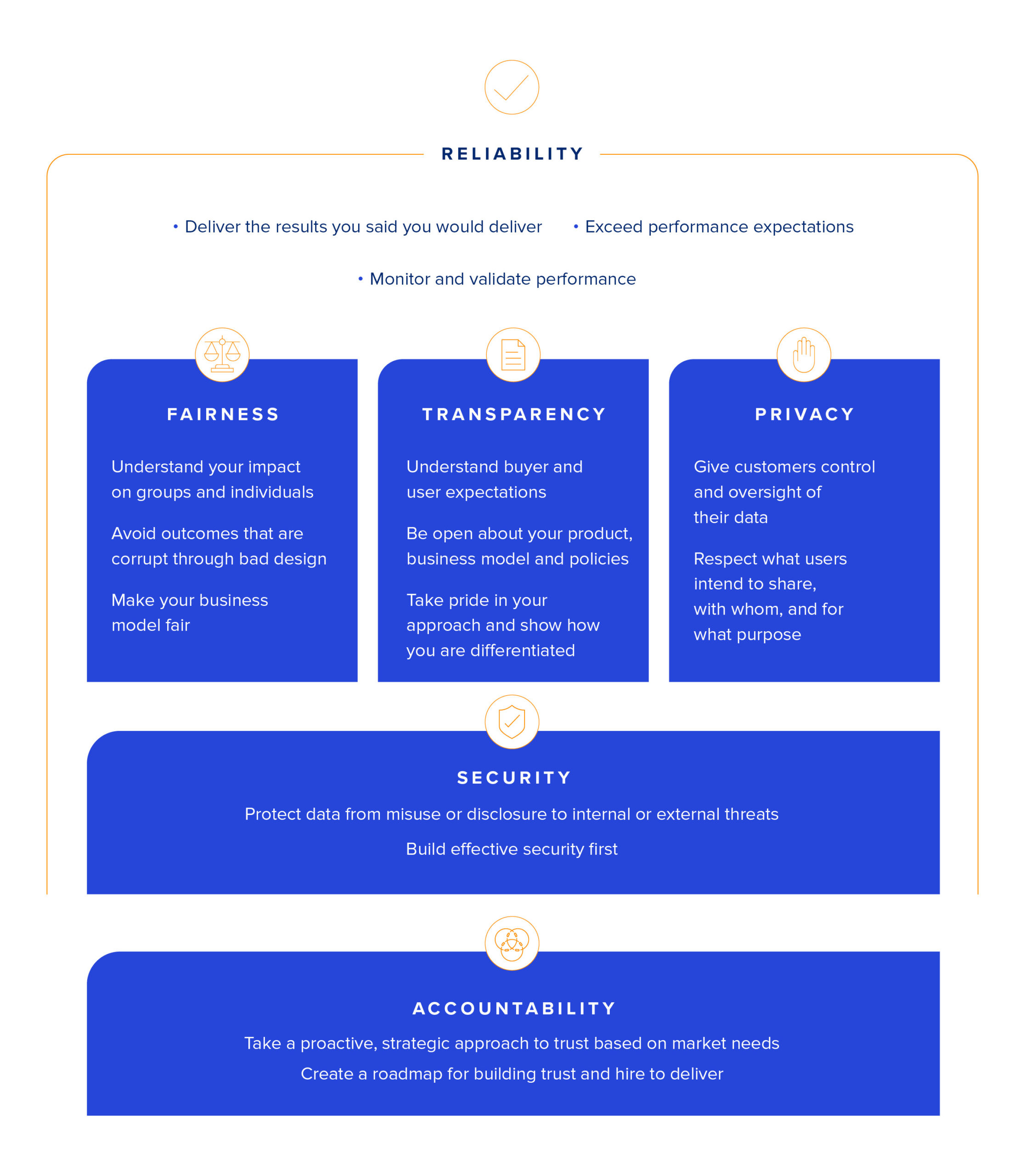
The 11 principles we outline in this playbook look at different aspects of trust, exploring accountability, security, privacy, reliability, fairness and transparency. For each principle, we've included three maturity levels so you can assess where you land today and a case study to bring the theory to life.
You can navigate using the content bar on the left, or by clicking the NEXT button at the end of each section.
We'll start by asking why trust matters so much to software companies today.
Why Trust Matters.
Are there any software companies that you would voluntarily trust to protect your most intimate personal details? Do you trust them because you believe they’ll do everything in their power to protect your information or simply because their services are so integral to your life that you feel you have no other choice? Unfortunately, many of us have resigned ourselves to sharing data even though we feel increasingly uncomfortable about it.
It wasn't always like this. Software companies used to be implicitly trusted with customer data, but a wave of high-profile scandals has made everyone wary of sharing information at a time when companies need it more than ever to train models, extract insights and drive automation.
This status quo is not inevitable. As a data-driven business, you have an opportunity to earn the trust of your customers, partners and regulators.
Trust is particularly important for software companies that build products using machine learning and artificial intelligence (AI). It allows companies to access the data that they need to fuel models and ultimately power AI solutions. However, AI also presents new challenges for trust. Since much of the data that companies use to train AI is generated by humans who are often themselves biased along racial, gender or other lines, there’s a risk that this bias can become embedded in an AI model and propagated at scale. In addition, as AI techniques become increasingly complex, companies will need to figure out how to explain the choices of their models instead of simply assuming that users are happy to trust a black box.
We believe that this current state of affairs presents a clear opportunity for software vendors to differentiate on trust. Companies that emerge as trust leaders will be able to drive the discussion on how data should be collected, created, used and protected in their ecosystems over the coming years.
The New Era of Trust.
We believe that this current state of affairs presents a clear opportunity for software vendors to differentiate on trust. Companies that emerge as trust leaders will be able to drive the discussion on how data should be collected, created, used and protected in their ecosystems over the coming years. As a result, their customers will share more data, use more services, and remain customers for longer. In other words, how much your customers trust your company directly impacts your revenue, growth and retention.
With the heightened awareness of data privacy issues, other aspects of software, including the business models themselves, are being scrutinized. We believe that customers will increasingly demand that companies operate fairly and transparently in how they treat customers, employees and society as a whole.
More than ever, it’s important to be proactive, to take opportunities to build trust competitively and to challenge yourself to think how each action you take will increase or detract from your customers’ trust.
In the next section, we'll define what it means to earn the trust of your customers.
Earning Trust.
We think of trust as a careful balance between the value that you deliver and the comfort that customers experience when interacting with your company, brand and products. When these two factors come together, you get happy customers that keep coming back for more, and share their experiences with partners and friends. When they’re decoupled, you may briefly enjoy success, but eventually trust will erode and customers will look elsewhere for greater value or comfort.
The graphic below helps visualize the balance between value and comfort:
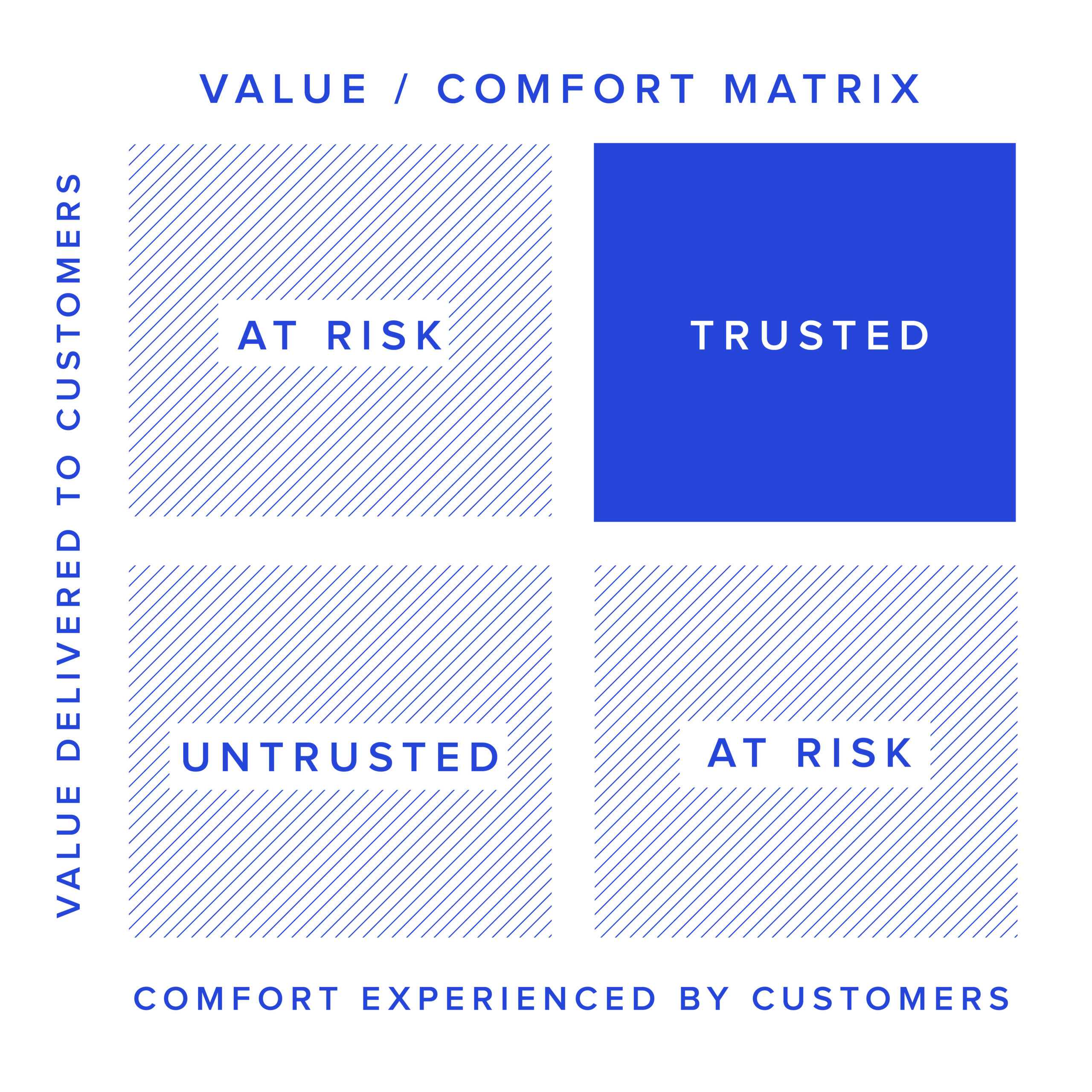
Companies in the top left deliver value. However, a security breach or a similar incident can materially impact customer retention, owing to a lack of comfort. In addition, companies in this quadrant can miss opportunities to acquire richer data from customers to enhance product capabilities.
Companies in the lower right have a good reputation or a surplus of comfort that they can leverage to deliver more value and move to the top right. The risk is not acting on the opportunity in a timely manner and losing on value to their competitors.
Drivers of value
Value is your core business proposition —
the reason why customers are driven to adopt your product. Some of the most common ways that you might deliver value to customers are:
- Improved top line.
- Improved forecasting/analytics.
- Improved product quality.
- Cost and time savings.
- Reduction of business risk.
- Reduction of uncertainty, complexity and friction of doing business.
Drivers of comfort
Comfort is peace of mind for your customers — the understanding that accessing the value that you provide won’t cause problems for them. Some of the most common aspects of comfort are:
- Reliability and stability.
- Responsible and secure data handling.
- Transparent business practices.
- Customer control of data and influence on product direction.
- Fair business model; shared vision
and purpose.
In the next chapter, we'll break trust down into its component parts and define some core concepts. This will make it easier to make an action plan based on specific outcomes.
A Framework for Trust.
Using the Framework.
For each principle in the sections below, we've included brief descriptions for three maturity levels and a case study. You can use the maturity levels to help you score your own organization. There's a full maturity framework at the end of the white paper.
Level
1
Level
2
Level
3
Capability and Ingredients
Your organization has intrinsic company characteristics, assets or strategic intent that give you an advantage for executing on trust. You have a basic understanding of priorities and opportunities, and there are few or no specialist skills within your organization.
Readiness and Process Advantage
You have formalized company standards, practices, procedures and skills that give you an advantage for execution. You have partially documented your approach and priorities, and acquired some specialized skills within your organization.
Execution Advantage
You’re exploiting advantages with mature processes that capture outcomes. You’re measuring trust and regularly checking your approach with customers to drive continuous improvement. Last, but not least, you have complete documentation of your approach, including roadmaps for implementation, and a complete set of appropriate skills to support the implementation of trust within your organization.
Case Study
While each company’s trust journey will be individual, the principles and maturity levels are designed to be generally applicable. To help illustrate how the principles can be used to chart a path toward increased trust, we will consider how a fictional start-up — PersonConnect — could progress to higher maturity levels in each area.
HR and recruiting are important areas for artificial intelligence (AI) investment, both because they are cost centers that benefit from efficiency improvements, and because hiring and empowering the right people is so critical to business success. AI promises to make things more efficient through process automation, and also to provide valuable insights, freeing HR teams from low-level tasks and helping them to operate in a strategic and data-driven way, and to build high-performing teams.
PersonConnect is an AI-enabled applicant tracking system and HR information system. Its chatbot engages prospective candidates and gathers information for their application, walks new hires through the onboarding process, and allows employees to ask questions about HR topics. HR teams can use the system to gather data on employee engagement and performance and hiring efficiency, and to automate standard HR processes.
Because HR data can be highly sensitive as well as highly valuable, the leadership team at PersonConnect wants to differentiate on trust. While the company has to date focused on building out the core functionality to compete with established players, it is now seeking to become the most trusted name in its space. Employees are excited about the new direction and have started to gather customer requirements, but the company has little established process and no plan for how to share its new focus with customers.
We will take PersonConnect through our trust framework and show how each principle contributes to a comprehensive trust strategy.
Accountability
Principle 1
Create New Value Through Trust.
Look for opportunities to create new business value through trust.
Level ONE
Level TWO
LEVEL THREE
You have spoken to and understand how to build trust with your customers.
You have built trust with existing customers.
You create new value through leveraging your trust with customers.
Building trust with your customers goes beyond compliance; it is about creating new value for customers and for the company. For example, building trust can lead to increased willingness for customers to share data with you, which in turn can be used to create new business value by training machine learning algorithms.
To prioritize opportunities to build trust, talk to your customers to understand the value they derive from your product and their degree of comfort with your solutions, practices and brand. Map your customers on the Value/Comfort Quadrant above to help identify those that are both at risk of churn (due to low perceived value or comfort) and strategic to the business. Next, take the necessary steps — whether by increasing the value you deliver or a factor of comfort — to reach trust. This will become your trust roadmap.
To increase value, you may need to build additional functionality. If functionality exists, but customers are not realizing value, you may need to address product reliability or reconfigure onboarding for these features to validate business outcomes and ROI cases.
How you build comfort with your customers will depend on your industry and the products that you offer. For instance, if you handle sensitive data, such as in healthcare and financial services, privacy and security may be top of mind for your users. If you are using AI to make high-stakes decisions, such as in fraud detection or recruitment screening, fairness and explainability may be major concerns.
Each incremental increase in the value you provide may require you to increase comfort to drive adoption. Conversely, increasing comfort can itself drive more value. For example, making systems more transparent with explanations can also improve customer satisfaction and increase product adoption. Keep in mind that situations that may seem like trade-offs don’t always need to be. Take advantage of win-win opportunities where you can enhance value and comfort at the same time (see Find Win-win Opportunities).
Be strategic in your investments and beware that excessive focus may start to yield diminishing returns. For example, addressing all potential security threats is impossible and could occupy valuable resources that would be better dedicated to more pressing threats to trust. The best companies find harmony between driving value, providing comfort, and efficiently using their limited resources.
Accountability
Principle 2
Build Trust Into Your Culture.
Operationalize trust through data values
and organizational governance.
Level ONE
Level TWO
LEVEL THREE
Your intent to build a trust culture is strong, but low on specifics.
You have specific values supported by training.
Your data values have become core to everyday operations.
Implementing trust in your organization requires that everyone understands the responsibilities that come along with access to customer data, starting with the CEO. To achieve this, unify and clarify your approach by writing your data values to explain how you think about and handle data.
Data values constitute a public commitment to customers and partners on how you will care for their data and respond in a time of need. When developing your own data values, align them with the sensitivity of the data being collected. In the next chapter, we've shared some example data values to inspire yours (see Share Your Data Values).
Without structures and processes to support proper data management, you leave your employees exposed to judgment calls. Instead, be clear on the expectations when handling sensitive data. Build a culture of trust where employees seek to do the right thing and feel comfortable questioning and challenging the status quo. Acknowledge and recognize employees who demonstrate success in the areas of trust.
Messages on trust should consistently and frequently come from the top — the CEO, C(I)SO or Chief Trust Officer. This makes it clear that trust is an organizational priority.
The extent to which senior leadership supports the objective of becoming a trusted company will directly impact your success.
New hires in all roles, from entry level to the C-suite, should be evaluated on not just their abilities, but also how much you can trust them with your organization’s and customers’ sensitive information.
Avoid delegating responsibility for trust across many individuals or teams. Problems arise when trust becomes a compliance or checklist item that is constantly traded off against other product priorities with no organization-wide coordination or authority.
The best companies will appoint a senior executive responsible for trust delivery. Where possible, they should report directly to the CEO. Even companies that have adopted the right way of thinking will still run up against conflicting interests. To be successful, the trust leader needs to have significant influence within the company. Ideally, the Chief Trust Officer (or equivalent) will also be an officer of the company and participate in leadership, marketing and product decisions.
Share your data values
Data values can vary significantly from company to company. Here are a few strong examples to inspire yours:
Data attribution and ownership — “Your data is yours.”
Data integrity — We respect original data and indicate when and how it is modified for the purposes of data standardization and enrichment.
Data purpose — We use your data for the agreed purpose and no other.
Product function and data privacy — We strive to improve our products while maintaining your privacy.
Control — We make it easy for you to decide what functionality you value, how you would like your data to be used, and when it should be deleted.
Fairness — We proactively identify potential sources of bias in the data before it is used in any downstream process such as model training.
Data retention — We do not retain your data any longer than needed for the purposes directly agreed with you.
Data sharing — We never share your data with anyone outside the organization without your explicit permission.
Security
Principle 3
Design Resilient Systems To Reduce the Impact of an Attack.
Assume that you will get hacked.
Level ONE
Level TWO
LEVEL THREE
Some knowledge and implementation of security principles exist in your organization.
Security principles are incorporated into your application architecture.
Security principles are fully incorporated into all processes and technology and are a key component of the company culture.
No system is impenetrable. The larger, more complex, and more visible the system gets, the more likely it is to eventually get breached. Three approaches that have been shown to minimize the impact of compromise are the principle of least authority, decentralization and redundancy.
The principle of least authority states that systems should never grant access to more resources than are required to complete the task. This is true for software, but also for human-based systems such as granting physical access to an office building after hours. Organizations should ask themselves whether the access is really required. If not, don’t provide that access, or limit it to certain times or certain physical areas.
Decentralization applies to both human processes as well as software architectures. When two individuals are required to approve a financial process or to add a user to a software system, a human process is decentralized. An example of decentralization in software architectures is found in bitcoin and blockchain, where the public ledger that tracks all transactions is distributed across thousands of nodes. For the integrity of the ledger to be compromised, 51 percent of those nodes would need to be controlled by a single entity, which becomes increasingly unlikely as the number of nodes increases. Decentralization can also be achieved with a micro-service architecture and structured design, which, in contrast to a monolithic system, can deliver security advantages by limiting access to data and other system resources.
Finally, redundancy helps to address increasingly common Denial of Service attacks, including attacks often executed by large-scale botnets. For example, top-tier cloud providers such as Amazon Web Services, Microsoft Azure and Google Cloud all provide logically and geographically redundant services, protecting against cyberattacks, physical breaches, and even natural disasters.
Security
Principle 4
Construct a Rapid Remediation Plan and Practice Using it.
When a breach occurs, be prepared to respond quickly and effectively.
Level ONE
Level TWO
LEVEL THREE
Your remediation plan has limited scope and applicability.
Your remediation plan is comprehensive and widely known.
You proactively update and practice your remediation plan.
Many organizations have formal plans for disaster recovery, but unfortunately most do not have comprehensive remediation plans in case of data compromise. When an incident does occur, the plans are often ineffective because they haven’t been tested and practiced ahead of time.
Investing in security will reduce the probability of needing to use the plans, but there will always be latent risks. Make it clear to customers and employees that you’ve taken reasonable steps to understand, manage and reduce these risks.
Effective plans cover both common scenarios and corner cases. They should include specific actions, quantifiable data, and steps to prevent similar incidents in the future. In the case of data compromise, plans will explain procedures for determining how data was affected and how the system may have suffered from being infiltrated.
When practicing the plan, be sure to involve all relevant stakeholders within the organization. The most effective drills don’t happen at predictable times of day, when everyone is at work. Try to make things as realistic and high-energy as possible. Hold live meetings with key people, including the CEO, CTO, and any software developers dealing with the incident. Include other teams such as customer success, sales, marketing, human resources and legal, all of which would play a role in a real incident.
Consider emulating a real breach by hiring professional “white hat” hackers to attack a replicated test environment that mirrors production. The more realistic your practice sessions, the more likely you will succeed during a real attack.
Yahoo! and Target are two examples that show how poor incident response directly affects the technical and PR damage of a major breach. In both cases, the companies had detailed incident response plans that proved to be poorly designed. Neither demonstrated a proactive response approach and, in the case of Target, it was reported that warnings were issued from its monitoring system and ignored before customer data was stolen.
When incidents inevitably do happen, use the learnings to re-prioritize and accelerate your security roadmap. Examine what failed in the organization that could have stopped the attack. Look at technology and process gaps, failures in the threat model, security awareness across the team, and the amount of resources allocated to mitigating threats. If the threat was known to be unmitigated, evaluate whether the damage incurred is consistent with your original estimate for this particular threat.
While we often read about data breaches, we rarely hear about the steps that companies take to fix them and improve their infrastructure. In 2014, JP Morgan Chase suffered a major data breach impacting 76 million households and 7 million small businesses.
By 2016, the company doubled its cybersecurity spending to more than $500 million, investing heavily in new technologies to strengthen its network and detection capabilities. Today, JP Morgan is regarded as the gold standard in both banking and cybersecurity, with more assets under management than any other North American bank. Even so, company officials understand the target on their back, with CEO Jamie Dimon identifying cyberattacks as the “biggest vulnerability… for just about everybody.”
Privacy
Principle 5
Understand Customer and Regulatory Privacy Requirements.
What you don’t know can hurt you. Get ahead of privacy issues, and reduce exposure by identifying and mitigating risks.
Level ONE
Level TWO
LEVEL THREE
You reactively respond to privacy issues with a compliance lens.
You proactively manage your data sources, considering both regulatory and customer requirements.
You not only map the risk landscape, but shape it proactively.
The most effective way to reduce your privacy risk is to avoid unnecessary data collection. If collecting personal data is a must, map out the data requirements and consider what might change the level of trust that has already been built with your customers. Extend your thinking to your partners and suppliers. Are there any transparency concerns around the origins of your third-party data? Conversely, could your practices be putting a downstream partner at risk?
With your data sources mapped, study the jurisdiction-specific privacy requirements and trends.
This is especially critical if your business operates in multiple geographic areas, as different jurisdictions often have different requirements around privacy, data retention and lawful access — sometimes even in direct conflict with one another.
The privacy discussion never stays still — new privacy-preserving techniques are emerging, and new regulations are under debate. Customer perceptions and demands also continue to shift as privacy violations figure prominently in the news. The best companies will continually refresh their understanding and adopt new technologies and practices.
Privacy
Principle 6
Give Customers Control and Oversight Over Their Data.
Show customers you care by providing user-friendly controls that are simple to understand.
Level ONE
Level TWO
LEVEL THREE
Customers can view or manage
their data by going through a manual support process.
Customers can view and manage their data easily.
You not only provide users with data usage controls, but educate and encourage them to help them make the best choices.
Consumer software companies have traditionally established very broad data rights in order to future-proof the business, following the philosophy that more data is better. Users often have little to no understanding, visibility or control over how their data is collected, stored, used or shared. However, this approach is quickly becoming incompatible with international legislation and increasingly, customer demands.
B2B software companies are typically at the opposite end of the spectrum when it comes to data rights. Most B2B companies have highly constrained contracts that limit or eliminate the possibility of cross-customer data aggregation and sometimes even prohibit using even an individual customer’s data to improve the system or services.
The most successful companies are those that create products that protect customer privacy by default. They review each data type they collect and ensure that it has a purpose, communicating the purpose back to the customer. Users understand how providing their data returns value and can easily opt in or out anytime they choose.
Your company should drive the conversation around consent and acknowledge that data ownership remains with the customer. It’s important to explain the value that you provide in exchange for access to each piece of data to inform your customers’ choice. Software teams should incorporate privacy into the development process and provide tools that give users visibility into personal data and how it is captured and stored.
An open dialogue around privacy encourages users to think about their data more frequently. When appropriate, remind users that an action has a privacy implication and ask whether they want to review their settings. For example, iPhone apps ask users to enable access to camera, microphone or location services only when this functionality is required. Social media platforms send alerts to check whether users want posts to be public or whether they would like to adjust their privacy settings.
Make settings optional and granular to encourage engagement. As users learn to trust the system and understand how sharing their information provides value back to them, they naturally become incented to share more and higher-quality information in order to get even more value from the system.
Fairness
Principle 7
Root out Bias.
Avoid propagating bias within your business, product and processes.
Level ONE
Level TWO
LEVEL THREE
You are informed about
bias and committed to
reducing it.
You have a robust set of
anti-bias processes throughout
the company.
You have quantifiable anti-bias KPIs supported by real-time reporting and monitoring.
Discrimination in all forms is under increasing scrutiny. Human bias can creep into your organizational practices when employees act on biased views, often without ever realizing it.
Increasingly, algorithmic bias also presents a challenge for companies that leverage AI. Machine learning is often portrayed as an objective, fair and data-driven approach to decision-making. However, fairness and objectivity only exist if data and models are free of bias. If your machine learning model is trained on biased data sets, your product or service will perpetuate unfairness and discrimination.
You can address human bias at the individual, team and organizational level. First, uncover individual blind spots by putting employees through self-awareness training on how to recognize their potential for implicit bias. For example, Harvard has an implicit association test to help understand deep-seated attitudes and beliefs.
When working in teams, diverse backgrounds and experiences draw different perspectives, which means that members will be more able and likely to uncover and challenge each other’s biases.
Address bias in your organizational processes by using objective data to decrease subjectivity in decision-making. For example, use data from psychometric assessments, job samples and a systematic multi-rater interview process to reduce bias in the hiring process.
To mitigate the effects of technological bias in your solution use both a top-down and bottom-up approach. When defining the problem being solved, think about how and why bias could come into play. Identify protected groups and determine how bias might impact each of them. Make sure fairness requirements are written into your design, with the explicit intention of testing for and eliminating the most impactful types of bias.
When collecting training data, be aware of biases in the data you are collecting or in the data collection and sampling methods themselves. Consider, for example, whether your model performs better for one micro-segment due to larger population samples. If so, consider collecting additional data for underrepresented segments, while being aware of the risks of access to sensitive user attributes. If you are relying on human annotators, define strategies for labeling data to minimize annotator bias, and design mechanisms to recognize bias in labels.
During model training, think about fairness as an optimization problem and test whether performance is optimized for underrepresented segments. Before deployment, consider using FairTest or other bias-detection algorithms to automatically identify unforeseen sources of bias. Finally, make sure you have an ongoing governance process that takes into account any changes to input data or model weights. You should also periodically check that your model complies with relevant fairness regulations.
Removing bias once you’ve detected it presents its own set of problems. Simply deleting sensitive attributes from a model does not solve the issue of fairness because there can be correlations between the remaining attributes and those sensitive attributes removed. It may also make it harder to representatively sample. Leverage existing academic research to achieve good representation in the data while simultaneously obfuscating any information about membership in the protected group.
Fairness
Principle 8
Develop a Fair Model for Value Exchange.
Look for opportunities to create new business value through trust.
Level ONE
Level TWO
LEVEL THREE
You are committed to developing a fair value exchange with
your end users.
You are implementing a fair value exchange in terms of value and comfort.
You constantly reinforce a fair value exchange for your company and ecosystem.
Create business models that are quantitatively and qualitatively fair to set up long-term business partnerships with your customers. Think carefully about what you need from your customers (e.g., data) and what you will offer to your customers in exchange (e.g., insights).
The best companies design reciprocal value exchange into their solutions.
If you’re not able to provide value immediately, stagger your data collection over time. As your relationship deepens and you collect more data, ensure that you provide more value in return. Simply put, if customers feel that they are not getting sufficient value from the product, any issues around comfort will be more acute.
Companies should also pay attention to the fair exchange of value with the community in which they operate, their employees (and contractors and suppliers) and with the environment. Consider the possibility of unintended consequences, and take responsibility for how your product and team respond. For example, would your solution or organizational policies behave fairly and compassionately in extreme circumstances, and do you have a mechanism for ensuring human oversight?
Would you be willing to lower business returns in a crisis to preserve trust? In August 2018, Verizon was widely criticized for throttling fire department data usage during California wildfires.
Companies might also want to consider if there are special risks in using your product that might apply to minority groups, different genders, different age groups, people with disabilities or others. For example, a model to predict the next CEO for a start-up developed by Mattermark predicted white males would be most likely to become CEO because the training data contained many more historical examples of this.
How might a malicious, dishonest, biased or purely profit-driven actor use your product? Could it impact others negatively? What policies or processes do you need to have in place to protect your users?
Once you’ve established a fair business model, clearly communicate the costs and benefits so that users can make an informed choice. If there are risks to using your product that you are aware of, share this information with users.
PersonConnect seeks to add value for managers.
Having done some legwork to understand customer perceptions of value, PersonConnect is currently at Level 2. It is beginning to move toward Level 3 by identifying issues important to maintaining a fair value exchange in future.
HR teams tell PersonConnect that they value the product, because it takes away rote queries and paperwork. This frees their VP HR customers to concentrate on more complex issues. Individual contributors and job candidates appreciate the system, because they can get answers to their questions immediately.
Through customer research, the team identifies one user group where the picture is less rosy. The team discovers that HR managers see PersonConnect unfavorably because they spend a lot of time inputting data into the system, but they cannot get the data they need for reports because the report builder is too rigid for their needs. The team discovers that many HR managers export data to Excel to build their reports. PersonConnect decides to create a series of most commonly used reports specifically for HR managers.
To further ensure a fair business model, PersonConnect’s trust team also spends some time thinking through extreme scenarios that might happen when its product is used. As the product gains increasing functionality, will it begin to replace human HR workers altogether? What happens if employees pose extremely sensitive issues to the chatbot that it doesn’t know how to handle, such as reporting ethical violations? The team has not come up with definitive answers to these difficult questions, but plans to regularly review them and discuss them with customers to show that they are aware of the issues. Their Head of Product also joins an industry working group that is laying out a vision for how AI-enabled HR products can help HR workers take on more strategic and consultative roles.
Reliability
Principle 9
Make Trust Measurable.
Use metrics to track your objective performance and demonstrate reliability to users and employees.
Level ONE
Level TWO
LEVEL THREE
Trust metrics are limited and ad hoc.
You regularly produce a comprehensive trust scorecard.
Your trust scorecard updates in real time and is proactively shared with all stakeholders.
Make trust measurable by setting objectives for the value and comfort you deliver for each component of trust, from design to transparency.
As you develop measures of trust, take stock of the actions your company takes to promote trust. For instance, you might record the number of security issues investigated, number of customer interactions discussing trust, or employees trained in aspects of trust. Add a discussion on trust to meeting agendas, project plans and roadmap discussions and track the actions they produce. This shows that trust is part of the day-to-day business and will help as you assess problem areas: are you underinvested or are your processes broken?
It is also important to assess the organization’s achievements in each area. You might track how accurately models performed or how quickly customer requests were fulfilled.
Organizations should also develop quantitative and qualitative measures of customer trust. Use case studies with ROI to quantitatively measure the value you provide.
Qualitative techniques and surveys show how your users perceive your trustworthiness — both the value they accrue and how comfortable they are using your service. Use the insights to improve internally and to learn how to talk to customers about trust.
No matter which metrics are important to your company, make sure they incentivize positive behavior and do not encourage unintended undesirable outcomes.
When evaluating technical performance, start with industry best practices and standards to guide you. For instance, in machine learning and AI, this means validating models and measuring and reporting on their performance using metrics such as precision, recall, F-score and AUC10. Where necessary, go beyond these standards and create or adopt new ones that help with the objective analysis of different aspects of the system and your business as a whole.
Once you are tracking these measures, the next step is to share them with relevant stakeholders to lead the conversation and show your accountability.
[10] Precision is the fraction of correct instances among all instances predicted. Recall is the fraction of instances correctly predicted among all correct instances. F-score is the harmonic mean of precision and recall. AUC measures the trade-off of precision and recall for binary classification. These are some examples of metrics in ML; usually each task in ML has its own set of evaluation metrics.
Reliability
Principle 10
Anticipate the Unexpected.
Things will go wrong. When they do, make sure you’re well positioned to minimize the impact.
Level ONE
Level TWO
LEVEL THREE
You analyze and respond to failures.
You proactively plan to contain fallout from failures.
You detect and respond to failures quickly and efficiently.
Your reputation and the trust of your customers is built on reliable and consistent product performance. Even with the best of intentions, every company needs to be prepared for when things go wrong. It’s not possible to predict the unexpected, but it is possible to prepare and build for business as usual in challenging circumstances.
How you anticipate, prevent and contain failures directly impacts your customers’ trust. When incidents do occur, many organizations fail to address the root cause, because they can’t get insights into what went wrong, or they don’t have a clear escalation process from support to senior leadership.
If you track system performance metrics and set thresholds to identify abnormalities, it’s easier to find and remedy the root cause to minimize the impact of failures. Continuous monitoring can help you see abnormal activity and investigate before things get out of control. You can also hire third parties to conduct penetration testing and audit the metrics you monitor.
The mindset of metric monitoring should be built into system design, so that when the metrics breach their threshold, systems automatically enter recovery mode and send alerts. This ensures that incidents do not get overlooked and deteriorate, unbeknownst to you.
Even still, you may have performance issues that are slipping through, but are noticed by your customers. Product usage data can reveal whether there is confusion around your workflows for you to improve. Setting up a social listening and customer feedback process will also allow you to track and respond to common issues.
It’s hard to create processes during an emergency, so be clear on accountability ahead of time. Clarify each employee’s role and function during recovery, and practice through drills. If there are rare and valuable skills on your team, ensure cross-training so that you have redundancy.
How you respond to adversity can buy you goodwill and build trust. When you face challenges, communicate openly and honestly about what has happened, who was affected and for how long, and what you have done in response.
Transparency
Principle 11
Explain Yourself.
Understand the explainability expectations of your buyers and users, and design your organization and its products accordingly.
Level ONE
Level TWO
LEVEL THREE
You’re motivated to understand the explainability requirements of your users.
You address the top explainability pain points.
Explainability is used as a competitive advantage.
Organizations have an opportunity to build trust by focusing on making systems, business policies and procedures, and products more explainable. The first step should be to understand market expectations around explainability for both the buyer as well as product users, who may not be the same people.
Examples of what product buyers may want to see include information on your organization’s cultural values and business ethics, supplier lists and any related selection criteria, hiring practices, and even documentation on internal processes such as how product features are prioritized.
For product users, an organization may have to provide information about why a particular recommendation has been made, an estimate of its impact, and even the ability to access an audit trail in high-impact automated decisions.
Develop an understanding of these groups including job roles, workflows, work environments, the lexicon they use, and any remaining pain points. Build your evidence by observing customers as they use the product and listen to sales calls to hear the needs of prospective customers. Once you adopt this mindset, apply it to your products as well as your organization, using interpretable models that make it possible to provide explanations. For some users, technologies that allow for greater explainability and more interpretable results are essential. For example, radiologists using assistive technologies need to see which areas of the scan it used to make the decision. Similarly, some regulations impose explainability requirements; for instance, the GDPR requires fully autonomous systems to explain every decision they make.
In general, people prefer short explanations — two or three bullets — that contrast the result against another. For example, for a credit score, you might provide two factors that would help to get a higher score, especially if one of them has disproportionately influenced the outcome. Or, for instance, you might show that you are basing a recommendation on data points of similar users.
Explainability should not come at the expense of model performance. Done well, both are possible. Those who have adopted explainability find several advantages. By better understanding the workings of the models yourself, you are able to generate and test hypotheses based on results, protect yourself from adversarial attacks, and monitor for bias.
Communicate your approach to trust
When all is said and done you have to talk to your customers to earn their trust. Let them know the value and risks of what you are doing in a way that’s easy for them to understand. Your communications should address what trust means to you, what your customers can expect from a partnership, and the specifics of your processes around trust.
Ethical and legal issues surround automation and AI, so be prepared to support your decisions with a comprehensive, clear and defensible approach. The questions that need to be answered are complex, so revisit your thinking regularly and be prepared to discuss and adapt your stance.
When describing what you've done, avoid using broad generalizations or meaningless phrases such as military grade encryption, complete transparency or we take security seriously. Instead, use simple and factually accurate descriptions of your controls and processes.
Trust is hard to build and easy to lose. No matter how well you do, there’s always a chance that things can go wrong. When they do, respond quickly and decisively using a crisis communications plan that builds trust instead of weakening it.
Conclusion.
Building trust with your customers is a significant opportunity to create mutual value through more productive relationships. To get there, you will need to deepen your understanding of what drives your customers and the value are they hoping to derive from your products and services. This will allow you to assess how you can create that value, what data you would need and what the best approach would be. Once you see the path to value, you can explore what would make your customers comfortable sharing that data and using those products.
The first step for any company looking to build trust with their customers is to understand where they stand today. The principles of trust and the associated maturity model can help you with that understanding and show how you can reach maturity in future.
Transforming your business around trust will not happen without a coordinated approach. Take a proactive, strategic, user-centric attitude. Design your trust program as a single initiative to ensure that your efforts around security, privacy, fairness, reliability and transparency are all focused on the same objectives. Finally, celebrate your approach to trust and share your successes and your struggles. An honest appraisal will help your customers to understand and appreciate your efforts.